Agent Tesla is a widely used Remote Access Trojan (RAT) written in .NET, known for its keylogging and credential-stealing capabilities. It primarily targets Windows users, extracting credentials from web browsers, FTP clients, and email applications.
Since its emergence, Agent Tesla has been leveraged in numerous cyberattacks, gaining momentum during the COVID-19 pandemic. It is commonly distributed via phishing emails and employs various evasion techniques to bypass detection.
In this post, we will analyze a live Agent Tesla sample, exploring its file system interactions, registry modifications, network behavior, and stealth tactics.
Setup & Initial analysis
For analysis purposes I’ve set up a Windows 11 virtual machine. Here is a list of tools I will be using:
Since I only have one monitor for the VM, I’ve arranged my desktop to keep Procmon, FakeNet-NG, Process Explorer, and File Explorer visible at all times (ex. 1).

Last thing before running the malware is to capture the first shot of the registry as the baseline for future comparison (ex. 2).
With the registry state saved, we can proceed with running the malware sample (ex. 3). Note that I’ve changed the name of the file to AgentTesla.exe for easier analysis.

I watched the tools for about 10 minutes while the sample was running, but there was too much noise to catch anything particularly interesting. At this point, I decided to stop logging and analyze what had been captured. I stopped FakeNet-NG, ended Procmon logging, and captured a second registry state.
In the process tree from Procmon, I saw that the sample did not spawn any child processes. At the same time, I noticed that the original AgentTesla.exe file had disappeared. To investigate further, I turned to Procmon logs to analyze its actions.
I noticed that the process SetRenameInformationFile is called. This particular operation when provided with a new path essentially moves the file.
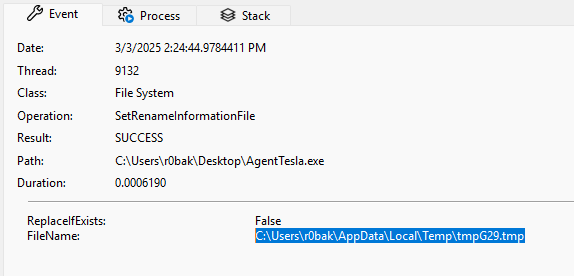
It is not uncommon for malware to use SetRenameInformationFile. Main reasons are evasion and persistence. To make sure we are in fact dealing we the same file, i’ve decided to run certutil, generating the MD5 file hash (ex. 4).
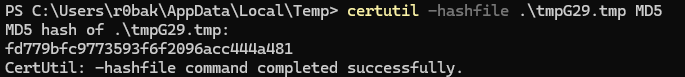
Seems like it matches the original file (MD5: fd779bfc9773593f6f2096acc444a481).
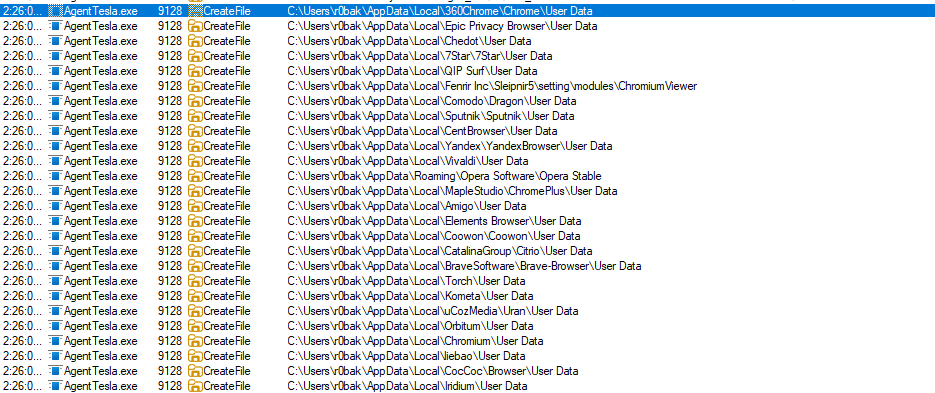
When seaching for more file operations I’ve stumbled upon multiple CreateFile operations (ex. 5) which seem to be enumerating subdirectories of \AppData\Local\, seaching for user data directories (related to popular browsers) to extract stored credentials, cookies and autofill information.
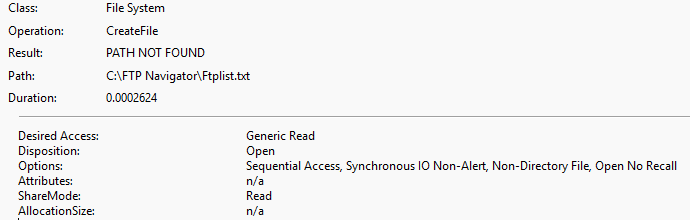
Digging deeper and another CreateFile operation was called (ex. 6) – this time to get access to FTP Navigator\Ftplist.txt which is a file owned by FTP Navigator – an FTP client. This action strongly suggests it’s attempting to harvest FTP credentials.
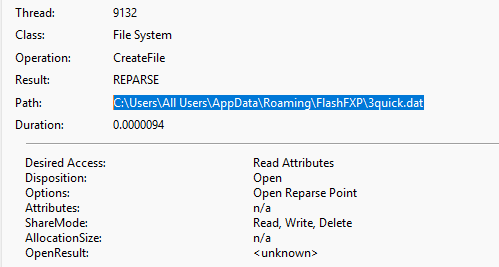
Only a few operations below the malware tries to access .dat file containing data of yet another FTP client – this time its FlashFXP (ex. 7)
On my VM, I have FileZilla FTP installed. Below (ex. 7), we can see that when the malware finds a file, it reads it until reaching the EOF (End of File) result.

There is a lot more files that Agent Tesla is trying to read data from so I’ll provide them in the summary section. For now lets move to the registry changes.
Registry modifications
Comparing the two Regshot captures revealed a total of 229 registry modifications. Now, it’s time to identify which ones are malicious. For the sake of clarity, I’ll only showcase the most interesting changes rather than listing all of them.
Deleted keys
Total of 5 keys were deleted, 2 of which are worth noting:
WMIProv refers to WMI (Windows Management Instrumentation) Provider, which logs system and application events. Malware often uses WMI for persistence, system info gathering, or executing commands filelessly. Deleting this key removes evidence of its WMI activity.
These keys store Group Policy service configurations. Deleting them could disrupt security policies or remove traces of policy modifications.
Keys Added
Out of 22 keys added, these caught my attention:
Seeing that this malware has previously deleted WMI logs, and now it’s adding new tracing keys could suggest abusing WMI for anti-analysis (removing logs), evasion, enumerating security policies and much more.
Below is a short example on how how WMI can be used for detecting VM/sandboxes (ex. 8). This could mean this sample is environment-aware and could alter it’s behaviour based on this factor.
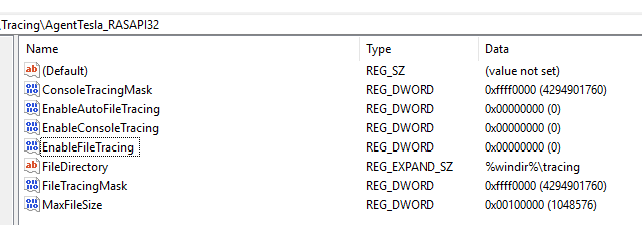
These registry keys get created the first time an application interacts with the Remote Access API, „rasapi32.dll„, and the Remote Access Connection Manager, „rasman.dll„. It means that Agent Tesla attempted network connection. Logging of the activity itself can be seen turned off under this registry path (ex. 9).
Values Removed
There is only one value removed:
This PID is linked to wmiprvse.exe. Removing this particular value could be an attempt at deleting records or hiding execution.
Other: Queried/Modified
There are also attempts at querying keys in procmon that show malicious behaviour.
Here AgentTesla.exe (PID:9132) tried to open a key in in Image File Execution options (ex. 10).
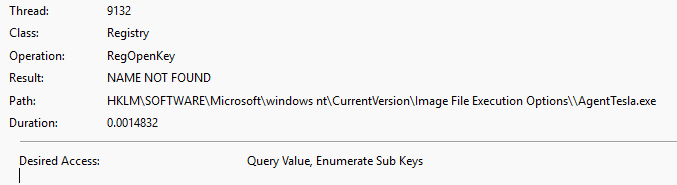
Accessing IFEO (Image File Execution Options) seems very suspicious because they are used when trying to debug a program – The fact that the sample tried to query it points to anti-analysis behaviour, it could detect if it’s running in debug mode.
Another very suspicious action is probing for GUID’s entries (ex. 11) under HKLM\System\CurrentControlSet\Control\WMI\Security
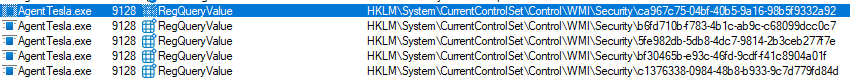
After some digging i found out that „ca967c75-04bf-40b5-9a16-98b5f9332a92″ corresponds to Windows’s ETW-based “Security.MitigationPolicy” instrumentation. Any unexpected querying of that GUID can be a red flag that an attacker is enumerating or attempting to modify Windows security settings.
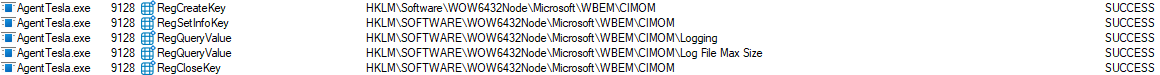
This sample seems to be doing a lot when it comes to evasion, here it tries to query and modify CIMOM (Common Information Model Object Manager) which controls overall WMI logging, not just individual providers (ex. 12).
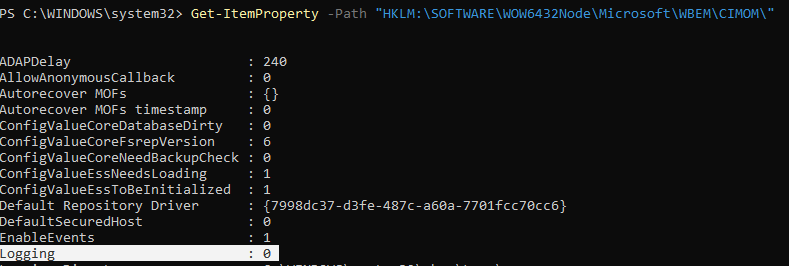
Just to confirm I checked the value of „Logging” – it is 0 (ex. 13). This is in fact a default value however the sample querying for it suggests it is checking for logging and potentially disabling it to evade detection.
Network Activity
AgentTesla.exe tried to establish TCP connection to some entity (likely the c2 server). It used multiple random source ports ranged 56185-56212 (ex. 13). The annotation here is „System Name:Port -> Destination IP:Destination Port”

To get more datails I decided to cross-reference this information with the .pcap file that was generated by FakeNet-NG. I opened it up with Wireshark.
Right away I can see a lot of ICMP traffic – but why exactly?
In networking it is a standard behaviour to generate ICMP error messages when TCP connection fails. In this example, the malware cannot reach it’s destination address so ICMP Type 3 (Destination Unreachable) code 1 (Host Unreachable) is generated (ex. 14).
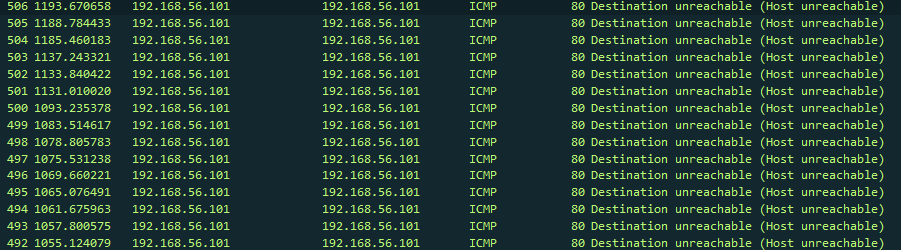
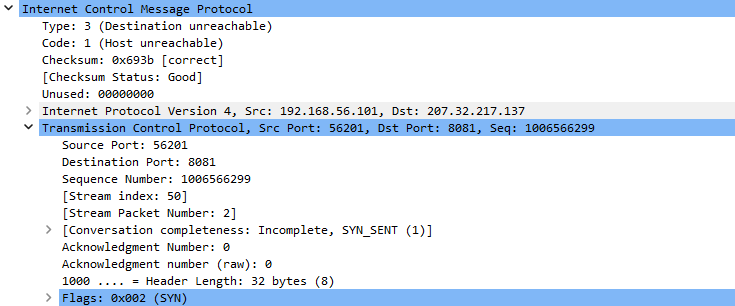
The ICMP packet contains part of the original TCP packet which can be seen as one frame in wireshark (ex. 15). All of these seem to be SYN packets to the malicious C2 server – trying to establish TCP connection (ex. 15).
Summary & MITRE ATT&CK
This dynamic analysis of the Agent Tesla malware sample revealed extensive credential-harvesting behaviour, registry modifications targeting WMI tracing and logging, and repeated attempts to connect with a remote command-and-control (C2) server. After running the malware in a controlled environment, the logs showed that Agent Tesla renames and moves its main executable to avoid detection, systematically scans directories containing browser and FTP credentials, and disables or modifies various Windows logging features to remain stealthy.
I’ve learned quite a bit about how Windows services, event tracing, and the registry interact – definitely an interesting experience!
Mitre Att&ck
Below are the tactics and techniques noticed during my dynamic analysis.
| Tactic | Technique |
| Execution | T1047 – has used wmi queries to gather information from the system. |
| Discovery | T1087 – collects account information from the victim’s machine. |
| Command and Control | T1071 – Application Layer Protocol: Web protocols |
| Discovery | T1057- can list the current running processes on the system. |
| Discovery | T1082 – can collect the system’s computer name and also has the capability to collect information on the processor, memory, OS, and video card from the system. |
| Defense Evasion / Discovery | T1497 – has the ability to perform anti-sandboxing and anti-virtualization checks. |
| Collection | T1185 – has the ability to use form-grabbing to extract data from web data forms. |
| Credential Access | T1555 – has the ability to steal credentials from FTP clients and wireless profiles. |
| Defense Evasion | T1564 – has created hidden folders, has used ProcessWindowStyle.Hidden to hide windows. |
| Defense Evasion | T1112 – can achieve persistence by modifying Registry key entries. |
And as promised, here is a more detailed list of providers/products from which this sample tried extracting data from:
Browsers
FTP Clients
Mail / Instant messaging
Other
Want to know more?
If you’d like to take a deep dive into technical aspects of topics from this article, here are my recomendations:
